Download XAMPP version 7.1.31 For Windows OS
Link: Download XAMPP Size: 144Mb Includes: Apache 2.4.39, MariaDB 10.4.6, PHP 7.1.31, phpMyAdmin 4.9.0.1, OpenSSL 1.0.2, XAMPP Control Panel 3.2.4, Webalizer 2.23-04, Mercury Mail Transport System 4.63, FileZilla FTP Server 0.9.41, Tomcat 7.0.92 (with mod_proxy_ajp as connector), Strawberry Perl 5.16.3.1 Portable Is This Helpful ? Say Yes or No in Comment Box… Read More : What … Read more
XAMPP Documentation
XAMPP is an easy to install Apache distribution containing MariaDB, PHP, and Perl. Just download and start the installer. It’s that easy. XAMPP is a free and open-source cross-platform web server solution package developed by Apache Friends, consisting mainly of the Apache HTTP Server, MariaDB database, and interpreters for scripts written in the PHP and Perl programming languages. Since most actual web server deployments use the same components as … Read more
Nagios Xi Download
nagios xi download virtual machine for windows vhd and ovf
Unable To Add SCHEDULED DOWN Time In (fan Nagios) Nagios.
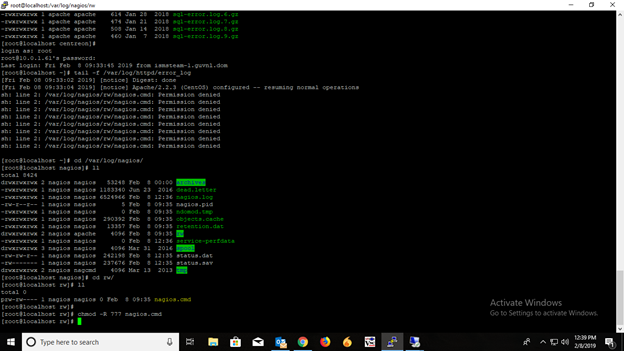
It is about the issue of permission with Nagios.cmd tail -f /var/log/httpd/error_log File location : /var/log/Nagios/rw/nagios.cmd After giving a 777 permission to this file my scheduled downtime is working fine. Look the screenshot below. For all type of monitoring and open source issue , Ask your query in comment box.
HOW DO I FOUND MY WINDOWS PRODUCT KEY
Windows 8.1 and Windows 10 The product key is located inside the product packaging, on the receipt or confirmation page for a digital purchase or in a confirmation e-mail that shows you purchased Windows. If you purchased a digital copy from Microsoft Store, you can locate your product key in your Account under Digital Content. Windows … Read more
NSClient++ Return Code Of 139 IS Out Of Bound…
This means something is wrong. To find out what is wrong you need to check the NSClient++ log file. The message means that an plugin returned an invalid exit code and there can be many reasons for this but most likely something is miss configured in NSClient++ or a script your using is not working. … Read more
How Do You Run A Script In Powershell?
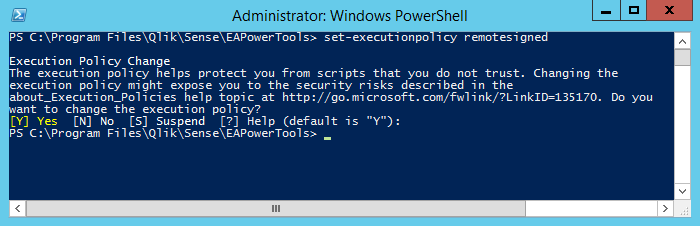
Run A Script In PowerShell? Launch Windows PowerShell, and wait a moment for the PS command prompt to appear Navigate to the directory where the script lives PS> cd C:\my_path\ (enter) Execute the script: PS> .\run_import_script.ps1 (enter) If it fails, you should check “setexecutionpolicy” Steps: Launch a Windows PowerShell window run as an administrator. Navigate … Read more
What are the process state in Unix ?
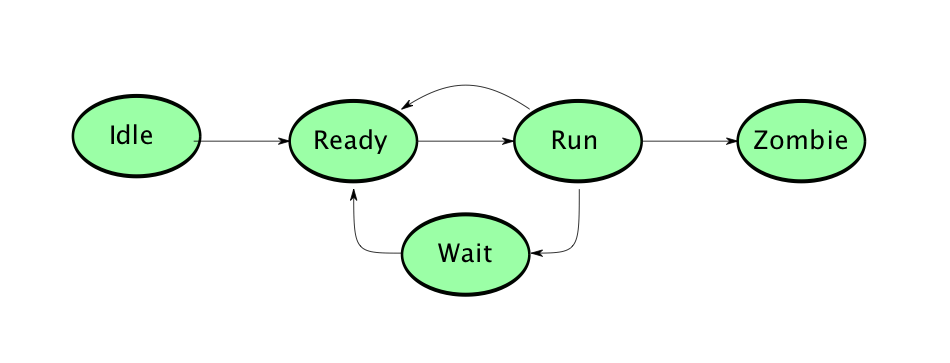
Source: http://www.cs.miami.edu What is the process state in Unix? This is a small experiment to show the life cycle of a Unix process. A Unix process is created in the idle state and is then moved between ready to run, running, and possibly waiting (or sleeping) , until it exits and becomes a zombie. Once … Read more
Penetration Testing(Pen Test) The Ultimate Guide
What is penetration testing? Penetration testing is an art. You can find out a lot of techniques and understand all of the tools, but the reality is that software is complex, especially when you start putting a lot of software systems together. It’s that complexity that means that there is no one-size-fits-all solution when it … Read more
WannaCRY Ransomware , How to keep your system safe
We will discuss about wannacry ransomware cyber attack and how to decrypt data which encrypted by wannacry. The WannaCry ransomware began to spread across the all over the Internet on Friday May 12th, 2017. I took my phone to see the text from my friend, “What should we do to beware the ransomware?” My … Read more
20 Common Protocols and Their Well-Known Port Numbers
The port number is a numeric identifier used to route packets to the correct application on a computer. Just as Media Access Control (MAC) addresses are used to deliver frames to the correct physical computer or you can say to the network adapter. And IP Addresses are used to route packets to the correct logical … Read more
Powershell – How To – SID To User
Step 1: Domain User to SID This will give you a Domain User’s SID $objUser = New-Object System.Security.Principal.NTAccount(“DOMAIN_NAME”, “USER_NAME”) $strSID = $objUser.Translate([System.Security.Principal.SecurityIdentifier]) $strSID.Value Step 2: SID to Domain User This will allow you to enter a SID and find the Domain User $objSID = New-Object System.Security.Principal.SecurityIdentifier ` (“ENTER-SID-HERE”) $objUser = $objSID.Translate( [System.Security.Principal.NTAccount]) $objUser.Value Step 3: … Read more
windows script to check Server Uptime
Description Ever wanted a simple HTML report showing you the UP/DOWN status of your servers? And for a little extra flavor how long that server has been up for? Some basic disk information? 1. Download the script to your favorite location and name it Uptime.ps1 2. Open a Powershell prompt and type: Get-Help pathtoscript\Uptime.ps1 –Full … Read more
Nagios Automation
FULLY AUTOMATED NAGIOS Let’s learn about automated nagios,which is pre-build ready with nagios,frontend and database installed monitoring for you… What is “Fully Automated Nagios”? Fully Automated Nagios (FAN) is a Linux distribution based on CentOS that comes pre-built with some of the most commonly used tools with Nagios. FAN comprises of a CentOS Linux distribution, … Read more
Offline Squid Proxy log analysis
Squid Access Log analysis with simple python command What is SquidMagic Master? squidmagic is a tool which is designed to analyze a web-based network traffic to detect central command and control (C&C) servers and Malicious site, using Squid proxy server and Spamhaus. Who is Spamhaus? The Spamhaus Project is an international nonprofit organization that tracks … Read more
Clear DNS Cache – How to Guide
DNS is a backbone of internet world. DNS Flush is a very common activity done by system engineers to resolve internet browsing issue. Here we are trying to explain various methods to clear
dns cache for Windows and Mac Operating Systems (Mac OS)
Honeywell Security – Pro-Watch Web Interface User Guide
The Pro-Watch Web Client User’s Guide provides the procedures and information necessary to install and use the Pro-Watch 4.3.5 Web Client. This guide is written for the Pro-Watch system administrators, Pro-Watch Badging Operators, and Pro-Watch Reporting Users. Pro-Watch The Pro-Watch platform is a complete access control system of hardware and software for small, mid-size, and … Read more
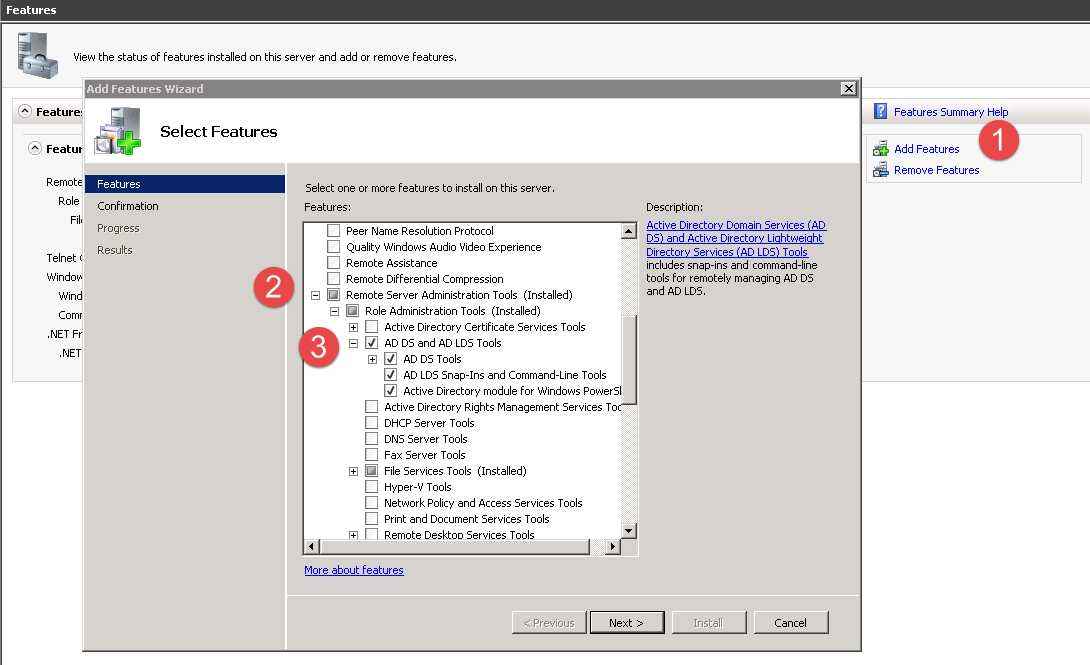
How to install Active Directory Users and Computers for Windows 2008
Windows Server 2008 Standard Instructions: Expand: Remote Server Administration Tools Role Administration Tools Active Directory Domain Services Tools Then check Active Directory Domain Controller Tools. Windows Server 2008 R2 Instructions: Expand: Remote Server Administration Tools Role Administration Tools AD DS and AD LDS Tools AD DS Tools Then check AD DS Snap-Ins and Command-Line Tools. … Read more
Manual Garbage Collection Process In active directory : Step By Step
You can use LDP.EXE to do the garbage collection control. Here are the steps: Step1: In Ldp.exe, when you click Browse on the Modify menu, leave the Distinguished name box empty. Step2: In the Edit Entry Attribute box, type “DoGarbageCollection” (without the quotation marks), Step3: In the Values box, type “1” (without the quotation marks). … Read more
You can install Linux apps in Google Chromebook Now !
Google confirms Chromebooks will soon be able to run Linux apps Developers will be able to write and publish code directly from their Chromebooks. Google’s Chromebooks will soon be able to run Linux apps and execute Linux commands following the company’s recent announcement that Linux support is coming to Chrome OS. The company’s flagship Chromebook, the Pixelbook will … Read more
Quickly Turn ON/OFF Windows Firewall Using Command Line
Windows Firewall on computers running Windows7, Windows 8 and Windows 10 is enabled by default. You may need turn it off/on for numerous reasons. steps for how you do it using a command prompt: To Turn Off: NetSh Advfirewall set allprofiles state off To Turn On: NetSh Advfirewall set allprofiles state on To check the status of … Read more
Best Offer Microsoft Certification Exams – 2018 !
Microsoft Exam Vouchers-Discount offers 2018 on MCSA,MCSE exams ! Professionals who have Microsoft certifications are some of the best paid employees out there. Get certified and start making more money: Microsoft certifications help grow your career. Automatically save 25% or 50% at checkout when you take two or more Microsoft Certified Professional exams … Read more
Opensource Network Monitoring
What is Nagios ? Nagios is a powerful monitoring system that enables organizations to identify and resolve IT infrastructure problems before they affect critical business processes. First launched in 1999. Nagios is officially sponsored by Nagios Enterprises Nagios monitors your entire IT infrastructure to ensure systems, applications, services, and business processes are functioning properly. In the … Read more
If You are using Microsoft Windows 8,windows 8.1 or windows 10 or Later OS, You need to download and install .Net Framework 4
Download Link : Download Here The Microsoft .NET Framework 4 redistributable package installs the .NET Framework runtime and associated files that are required to run and develop applications to target the .NET Framework 4. Version: 4 File Name: dotNetFx40_Full_x86_x64.exe Date Published: 21-02-2011 File Size: 48.1 MB The Microsoft .NET Framework 4 provides the … Read more